Proxy Servers: The Unsung Middlemen of the Internet
In 2025, global internet traffic surpassed 5.3 zettabytes, intensifying concerns over privacy, censorship, and network efficiency. Platforms like private residential proxies have emerged as critical tools, enabling both businesses and individuals to navigate the web securely and anonymously. These specialized servers act as intermediaries between users and websites, offering IP masking, controlled access, and traffic management — functions that have become essential in today’s complex online ecosystem.
Why Proxy Servers Matter
Proxy technology has moved beyond niche usage. A 2023 GlobalData report found that 35% of enterprise-level companies in North America rely on proxy servers for internal security, traffic monitoring, and regulatory compliance. Proxies allow users to maintain privacy, bypass geo-restrictions, optimize bandwidth, and protect devices from malware.
Key advantages of proxy servers include:
- Privacy Protection: Advertising networks and analytics platforms face difficulty tracking user activity.
- Access to Restricted Content: Geo-blocks and government censorship can be bypassed seamlessly.
- Traffic Management: Organizations can restrict employee access to approved web resources.
- Malware Protection: Incoming traffic is scanned for viruses and other malicious code.
- Faster Load Times: Frequently accessed content is cached, reducing load time.
- Bandwidth Optimization: Compressed data lowers network load and internet costs.
Services like private residential proxies provide real IP addresses from legitimate ISPs, offering high performance while maintaining strong privacy protections.
How Proxy Servers Work
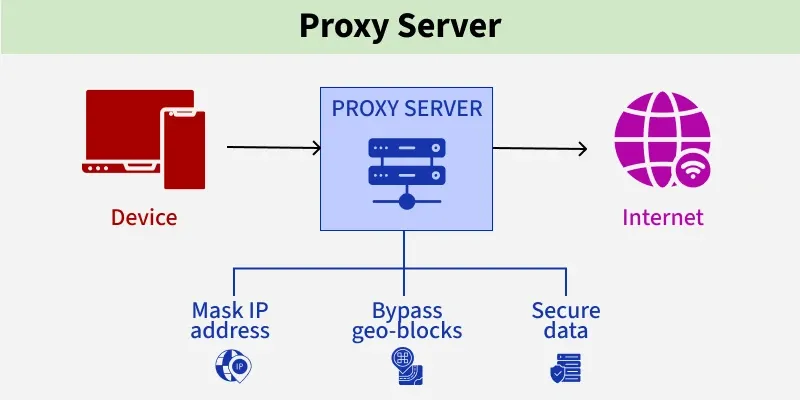
A proxy server functions as a filter for client web requests. When a user enters a URL, the request is sent to the proxy, which then:
- Forwards it to the target website.
- Retrieves content from its cache.
- Blocks access if restricted by administrative rules.
Depending on the type, a proxy can hide the client’s IP, leave it visible, or replace it with false data. Many users rely on proxies to mask their real IPs, a function often compared to VPNs, though proxies differ in encryption, protocol handling, and privacy guarantees.
After retrieving the requested data, proxies may also perform operations like malware scanning, compressing data, or caching content to improve speed and reduce bandwidth usage. This makes proxies especially valuable for businesses handling high volumes of web traffic.
Types of Proxy Servers
Proxies are categorized by anonymity, network placement, IP type, access level, and communication protocol.
By Anonymity:
- Transparent: Does not hide the client’s IP or proxy presence.
- Anonymous: Replaces client IP but identifies as a proxy.
- Elite/High Anonymity: Hides both client identity and proxy status.
- Distorting: Declares itself as a proxy but provides false client information.
By Network Position:
- Forward Proxies: Intercept traffic from clients to external servers.
- Reverse Proxies: Intercept traffic from internal servers to clients.
By IP Type:
- Data Center: Hosted in data centers with provider IPs.
- Residential: Uses real ISP-assigned IPs, often through services like private residential proxies.
- Mobile: Operates via cellular network IPs, simulating mobile devices.
By Access:
- Public: Free and accessible but less secure.
- Private: Paid, offering higher reliability and security.
By Protocol:
- HTTP: Handles unencrypted web traffic; supports caching, content filtering, and access control.
- HTTPS: Handles encrypted traffic but does not decrypt content, enabling secure browsing.
- SOCKS: A versatile protocol that handles multiple traffic types (TCP/UDP, P2P, FTP), ideal for bypassing firewalls and geo-restrictions.
Risks and Considerations
Despite their advantages, proxies carry risks. Users share sensitive data with the proxy provider, who may log, sell, or misuse it. Free proxies are particularly risky, but even paid services require careful vetting. Many proxies do not encrypt traffic, leaving it vulnerable to interception. Cybersecurity experts advise caution when sending sensitive information through unfamiliar proxies.
Conclusion
Proxy servers remain a cornerstone of digital privacy, security, and operational efficiency. Acting as firewalls, caching nodes, bandwidth optimizers, and anonymous gateways, they enable access to restricted content while masking IP addresses. Platforms like private residential proxies offer a combination of anonymity and legitimacy, making them valuable tools for businesses and individuals alike. However, users must exercise caution, understanding potential risks and selecting providers carefully to protect personal and corporate data.